Frank Wadsworth
Jul 24, 2024
Third-party engagements are integral to the functioning of modern businesses. However, they come with critical risks that must be managed to safeguard the company's operations, reputation, and financial health. A robust Third-Party Risk Management (TPRM) program is essential to mitigate these risks effectively. Below, we explore the key components and considerations for building and maintaining a successful TPRM program.
Understanding Third-Party Risks
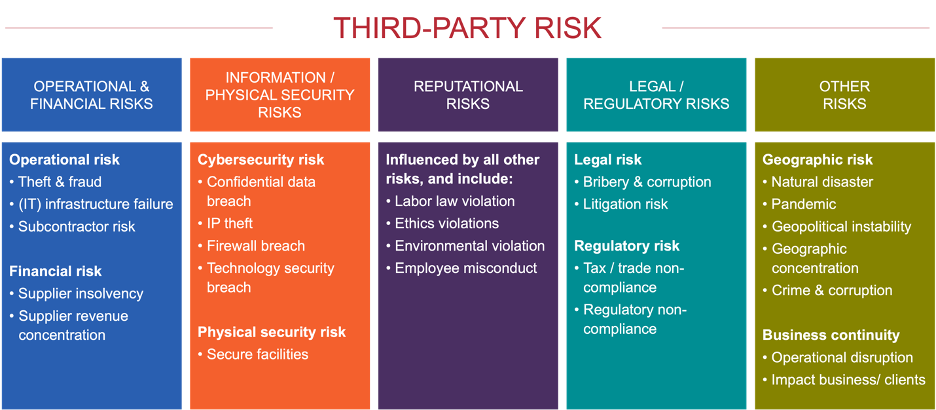
The foundation of any TPRM program lies in identifying and managing six primary categories of risk:
Operational & Financial Risk: This pertains to the operational stability and financial health of third-party vendors.
Information & Physical Security: Protecting sensitive data and physical assets from unauthorized access or breaches.
Legal & Regulatory Risk: Ensuring compliance with laws and regulations to avoid legal repercussions.
Business Continuity: Maintaining continuous business operations despite disruptions.
Geographic Risk: Considering the political, economic, and environmental stability of the regions where third parties operate.
Reputational Risk: The potential damage to the company's reputation, influenced by the other risk categories.
It is crucial to align these risks with your organization's risk appetite and tolerance, defining the acceptable levels of risk and the maximum that can be tolerated.
The Consequences of Loopholes in TPRM
Failing to manage third-party risks can lead to significant and costly consequences. High-profile breaches, such as UnitedHealth Group’s $872M loss in April 2024 ($1.6BN YTD August 2024) due to a cyberattack, executed via a vulnerable Citrix portal and impacting one third of Americans or the Capital One incident in 2019 where over 100 million credit applications were compromised, underscore the importance of effective TPRM. Similarly, the Target breach in 2014, which exposed payment and personal information for 110 million customers, was linked to a compromised heating and air conditioning vendor. These cases highlight the vulnerability of companies, regardless of size or industry, to third-party risks.
Regulatory Guidance and Compliance
The regulatory landscape for TPRM is becoming increasingly stringent, especially concerning data privacy and cybersecurity. Legislation like the California Consumer Privacy Act (CCPA) emphasizes protecting consumer data privacy. In the financial services sector, regulators such as the FFIEC, OCC, and DFS have issued detailed guidelines focusing on business continuity, subcontracting, and cybersecurity. Aligning your TPRM program with these regulatory requirements is essential to avoid significant penalties and operational disruptions.
Building a Robust TPRM Program
A successful TPRM program should be built across six dimensions:
Governance: Establishing a robust governance model with enforceable policies and procedures.
Strategy: Developing a strategic approach that aligns with business objectives.
Process: Implementing efficient processes for risk assessment and mitigation.
Risk Framework: Establishing a comprehensive risk framework.
Tools & Analytics: Leveraging advanced tools and analytics for real-time risk monitoring.
Implementation & Change Management: Ensuring effective implementation and adaptability to change.
It is crucial to identify, assess, and mitigate risks at the speed of business, enabling rather than impeding business operations.
Rule-Based Segmentation and Risk Assessment
Not all vendors and suppliers pose the same level of risk. It is important to use a rule-based model to quickly identify and assess the critical and high-risk third parties. Generally, about 5-10% of your third-party population will meet this criterion. Continuous monitoring and risk sensing are essential to manage these critical suppliers effectively. Establish/leverage supplier risk dashboards that utilize real-time data and predictive analytics to manage supplier risk, providing insights into social media sentiment, negative news alerts, company litigation, geographical risk, financials, and supply chain relationships.
Ensuring Business Continuity
The COVID-19 pandemic has highlighted the importance of supply chain resilience. According to the National Association of Manufacturers, 78% of manufacturers in the U.S. were financially impacted by COVID-19, with 35% confirming supply chain disruptions. While we cannot fully mitigate the risk of events like COVID-19, we must consider such catastrophic events in our risk planning, ensuring business continuity and disaster recovery plans are adaptable and robust.
The Criticality of Third-Party Dependencies
Understanding and managing critical third-party dependencies is vital. A small but essential component supplier can significantly impact business operations if non-compliant or disrupted. It's not the size of the supplier that matters but their potential impact on your business. Ensuring compliance, maintaining sufficient inventory, and working closely with critical suppliers are key to mitigating such risks.
Conclusion
Effective Third-Party Risk Management is essential for safeguarding business operations, maintaining compliance, and protecting reputations. By understanding and addressing the six categories of risk, adhering to regulatory requirements, and building a robust TPRM program, organizations can manage third-party risks effectively and ensure business continuity.
Ready to Transform Your Third-Party Risk Management Program
Visit us at Hatfield Advisory to learn more about how we can help you transform your TPRM challenges into opportunities or contact us directly via our contact page.
About Hatfield Advisory
Hatfield Advisory offers tailored insights and strategic guidance on optimizing operational processes, specializing in procurement, third-party risk, supply chain, and outsourcing advisory services. At Hatfield Advisory, our client-centric approach integrates rigorous analysis, strategic thinking, and pragmatic problem-solving to empower organizations to overcome challenges and achieve sustainable growth.